In this article:
Before you start
- Why use two-factor authentication (2FA)
- How does it work?
- How to login with Email authentication
- How to login with an Authenticator app
- How to switch between two authentication methods
Why use two-factor authentication (2FA)
Two-Factor Authentication (2FA) adds an extra layer of protection to your account. It strengthens its security by making it more difficult to access. With two-factor authentication, you must provide two different and independent pieces of information (a password and a verification code) to confirm your identity. This therefore prevents someone who knows your password from accessing your account without your authorization. Even if it is compromised, no one can log in without also having access to your second authentication method.
How does it work?
In addition to your usual password, you will need to enter a 6-digit verification code sent by email or generated by using an authenticator app during the login process.
However, it is not necessary to enter a verification code on devices that you believe to be trustworthy and that you have registered as such.
Learn how to add or remove trusted devices >
How to login with Email authentication
A verification code will be sent to the email address you provided. You can use a different address than the one associated with your user.
How to login with an Authenticator app
If you don't already have one, you'll need to download an authenticator app on your mobile device, such as Google Authenticator, Microsoft Authenticator, Duo Mobile, or Authy. These apps generate security codes and allow you to log into accounts with two-factor authentication.
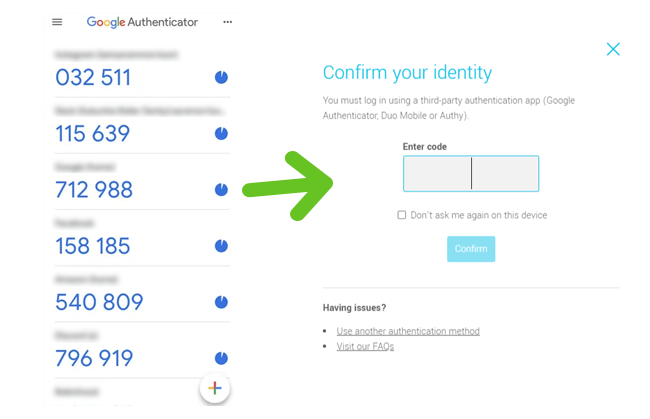
How to switch between two authentication methods
It is possible to set up more than one two-factor authentication method. For example, you can decide to enable the email authentication method and to also use an authenticator app. However, to log in, you will only need to enter one verification code. By default, we will ask for the one generated by the last authentication method used. You can switch from one method to the other by clicking the Use another authentication method link.
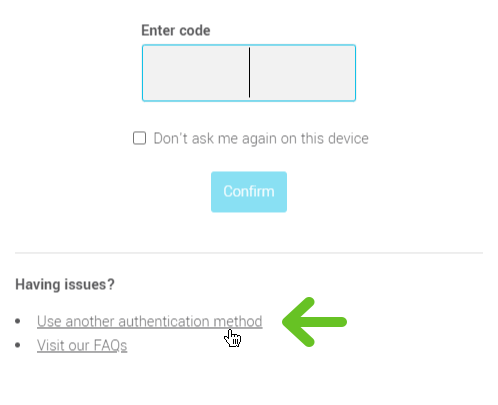
Setup your two-factor authentication methods
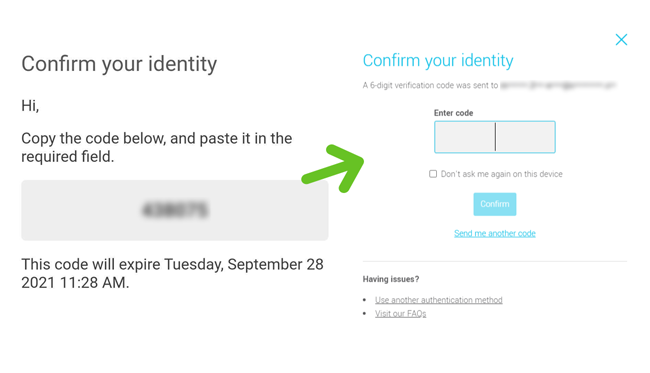
Activate your email authentication
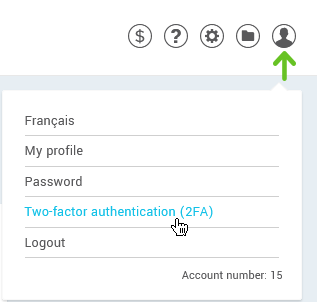
- Log into your account.
- Go to .
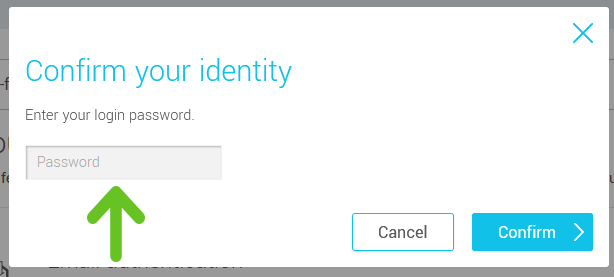
- Enter your password to confirm your identity.
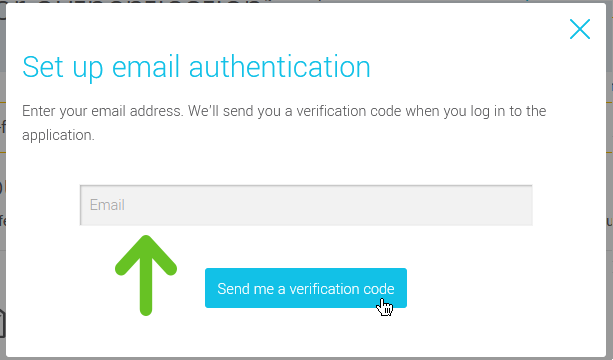
- Enter your email address and click Send me a verification code. We’ll use this email to send you a verification code when you log in to the application.
- Check in your inbox. You should have received an email containing a 6-digit verification code. Enter this code in the appropriate field.
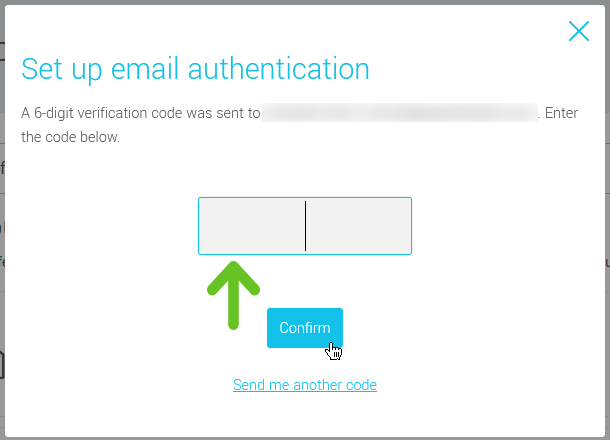
- Click Confirm to complete the email authentication configuration.
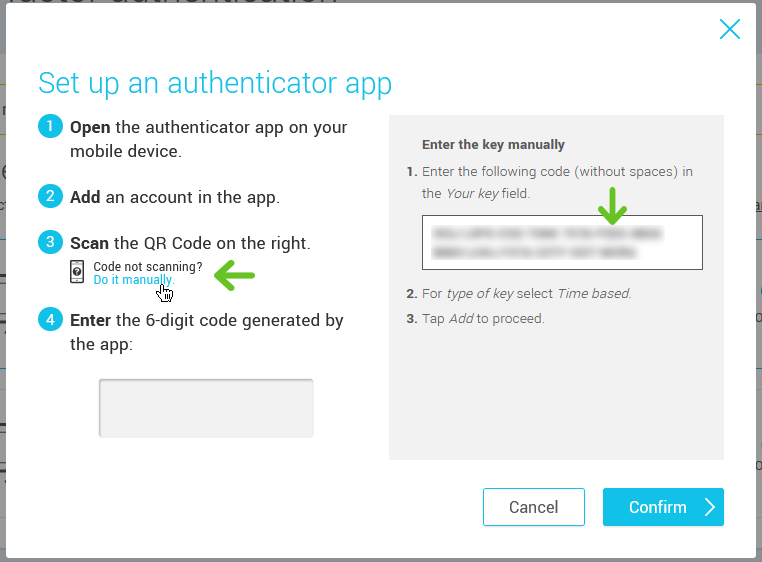
Setup your authenticator app
- Log into your account.
- Go to the menu.

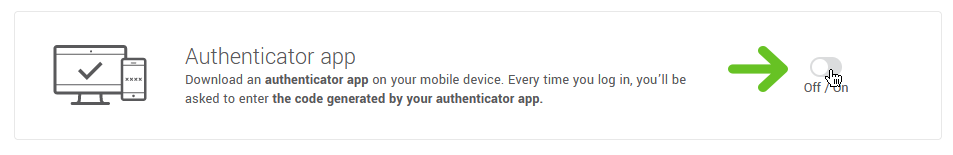
- Turn the Authenticator app switch on.
- Enter your password to confirm your identity.

- Open your authenticator app and add a new account. (The method will differ from one application to the other. Make sure to follow the steps on your screen).
- Scan the QR code on the screen with your mobile device.
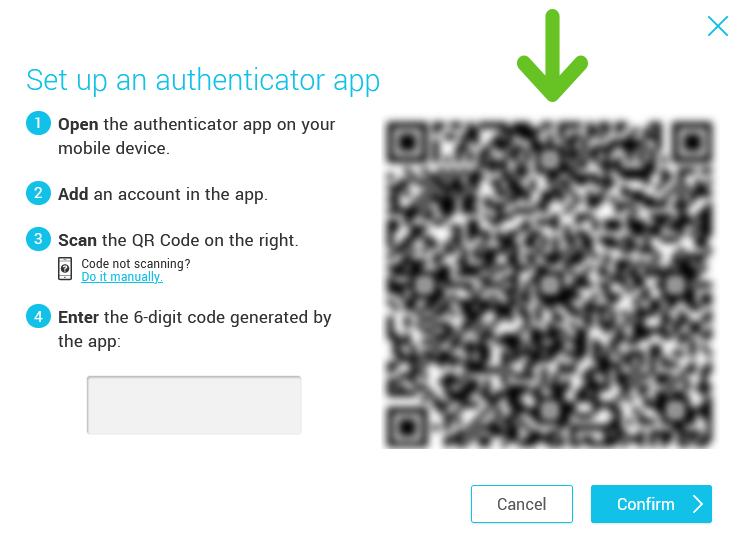
- Enter in the popup the 6-digit code generated by your authenticator app.
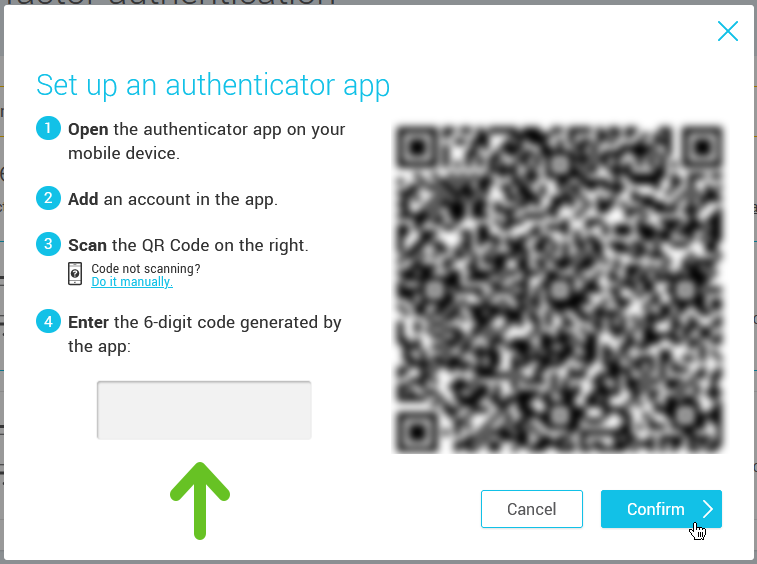
- Click Confirm to finish the setup.
Add or remove trusted devices
If you use your personal computer, follow basic internet security (frequent antivirus scans, no downloads or clicks on unknown links, etc.) and don't share it with other people you can decide to add it to your trusted devices. When you use a device on that list, you don't have to enter the two-factor verification code to log into your account. You only need your password and username. If something changes, please note that you can remove at all times access to a trusted device so that it will start asking you again to use two-factor authentication.
Add a trusted device
Simply check the box Don't ask me again on this device when logging in.
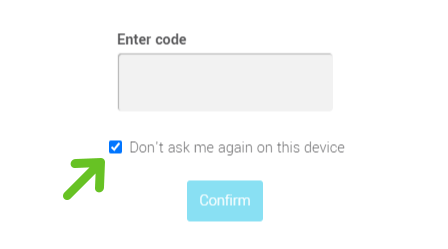
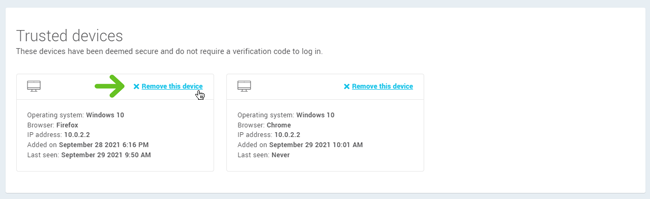
Remove a trusted device
Go to . Click Remove this device, then Yes, remove to confirm your action.
Modify or remove a two-factor authentication method
Modify email address
Go to . In the Email authentication section, click Modify email address and follow the steps on the screen.
.png)
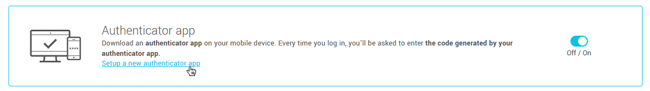
Setup a new authenticator app
Go to . In the Authenticator app section, click Setup a new authenticator app and follow the steps on your screen.
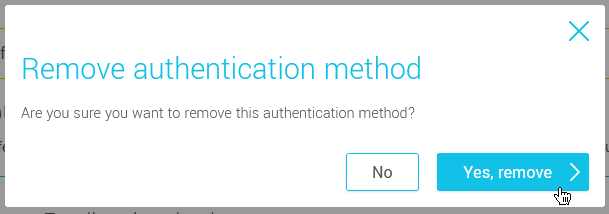
Remove an authentication method
Go to . Turn off the switch beside the authentication method you wish to deactivate. Input your password and confirm your choice by clicking Yes, remove.

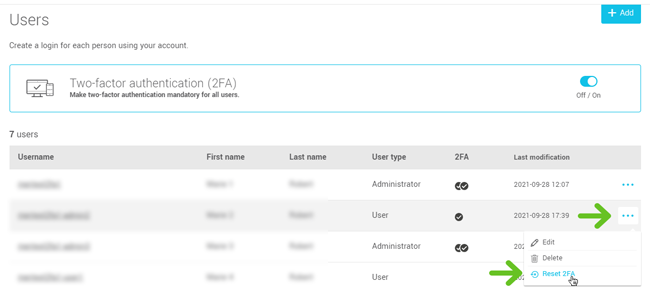
Reset a user's two-factor authentication methods
If an account user doesn't have access to their authentication methods and can't login, it's possible to help them by resetting their two-factor authentication methods. They will be prompted to set up a new authentication method at their next login.
How to proceed
Go to and open the menu on the right of the user, then click Reset 2FA and confirm your action by clicking Yes, reset.
Learn how to recover access codes >
Frequently asked questions
- What can I do if I don't have access to my email or my authenticator app anymore?
- Why can't I see the option to make two-factor authentication mandatory for all users?
- How can I use another authentication method when I am logging in?
- Why can't I remove the last authentication method for my user?
- I share my access code with another person, can I still set up my two-factor authentication?
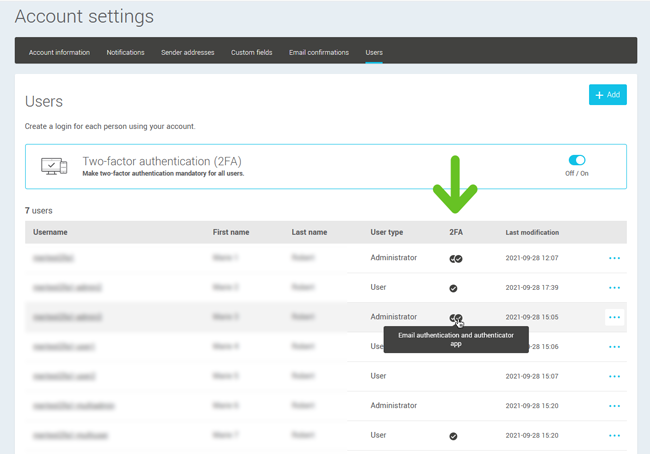
- How can I see which users have activated the two-factor authentication?
What can I do if I don't have access to my email or my authenticator app anymore?
Contact one of your account administrators so they can reset your two-factor methods to help you. If it's not possible or you still are unable to enter your account, contact a member of our technical support team for further assistance.
Why can't I see the option to make two-factor authentication mandatory for all users?
You need to be an account administrator in order to access this function.
How can I use another authentication method when I am logging in?
We'll only ask for one verification code even if you have set up two authentication methods. By default, we'll ask for the code generated by the last method used. To switch to the other method, click the Use another authentication method link.

Why can't I remove the last authentication method for my user?
If you're unable to remove the last authentication method remaining for your user, it's because the two-factor authenticator has been deemed mandatory for all users in your account. To find out how to access the option in order to deactivate it >
If the option is not visible for you, contact an account administrator.
I share my access code with another person, can I still set up my two-factor authentication?
You can, but you need to make sure to use a method you both have access to, such as a common email address. To keep your account secure, we strongly suggest that each person needing to access the account have their own access codes. Learn how to create a user >
How can I see which users have activated the two-factor authentication?
Go to to see the list of all users in your account. In the 2FA column, there will be a checkmark besides users that have already activated at least one authentication method. Hover over the checkmarks icon to see which method was activated for each user.