In this article:
Before you begin
About SAML SSO
SAML SSO (Single Sign-On) lets your users sign in to Cyberimpact with their Microsoft Entra ID (formerly Azure AD) identity—or any other identity provider (IdP) that supports SAML 2.0—so they don’t need a separate Cyberimpact password.
This approach centralizes and secures access to Cyberimpact. It reduces password-related risks, simplifies access to your internal tools, and automatically applies your security policies (MFA, restrictions, etc.). When someone leaves, you remove their access in Entra ID and they can no longer sign in to Cyberimpact (their Cyberimpact profile is not deleted automatically).
This article walks you through configuring SAML SSO with Microsoft Entra ID. If you use a different SAML provider, please contact our support team for the appropriate steps.
Prerequisites
-
A Cyberimpact account on the Pro plan.
-
Each user must have a valid email address as their username.
-
That email address must match the one used in your identity provider (IdP), such as Microsoft Entra ID.
-
You must have administrator rights in your Microsoft Entra ID tenant to create/configure the SAML application.
-
To enable SAML SSO for your account, please contact our support team. It is not yet possible to manage SSO configuration directly from your Cyberimpact account.
-
The request must be submitted by an account administrator or the primary contact.
-
Cyberimpact will provide you with:
-
Return URL (ACS — Assertion Consumer Service URL)
-
Entity ID (service identifier)
-
-
From your side, you will need to send us the following information so we can complete the setup:
-
IdP Entity ID
-
IdP Login URL (SSO URL)
-
IdP Logout URL (optional)
-
IdP X.509 Certificate in Base64 format (Certificate (Base64))
-
-
Required attribute your IdP must send: the user’s email address (mandatory), either as the NameID (emailAddress format) or as an email attribute.
What you should know
-
SAML 2.0 compatibility — Cyberimpact works with Microsoft Entra ID (formerly Azure AD) and any SAML 2.0–compatible identity provider that supports manual configuration. At this time, Cyberimpact does not offer native IdP integrations.
-
Enabling SSO does not automatically add users from your identity provider into Cyberimpact. An administrator must create users in Cyberimpact and assign their roles and permissions.
-
For someone to sign in via SSO, they must be assigned to the SAML application in your identity provider (IdP), such as Microsoft Entra ID.
-
Once a user is configured for SSO, their Cyberimpact username and password no longer work. They must sign in via SSO only.
-
Users in your account who are not assigned to the SAML application in your IdP can still sign in with their username and password.
-
You can make SSO mandatory for your account. In that case, only users who are assigned in the IdP and whose email address matches the attribute sent by the IdP can sign in (via SSO). All other users will not be able to sign in.
-
External users (guests) are not affected by the “Mandatory SSO” option. They continue to access their account with a username and password. If you want to require SSO for them, remove their guest access, create them as regular users in your Cyberimpact account, then add them to your IdP.
-
If you remove a user’s access in the IdP (e.g., when someone leaves), they can no longer sign in to Cyberimpact. Their profile is not deleted automatically in Cyberimpact; you can disable or delete the user in the app if needed.
About two-factor authentication (2FA)
After signing in via SSO, the user must still enter their Cyberimpact 2FA code, as this security step is mandatory. The 6-digit code can be received by email (default) and/or generated by an authenticator app. If the user marks their device as trusted, they won’t be prompted for the 2FA code again for 30 days on that device.
Configuration steps in Microsoft Entra ID
Create a Non-Gallery Enterprise Application
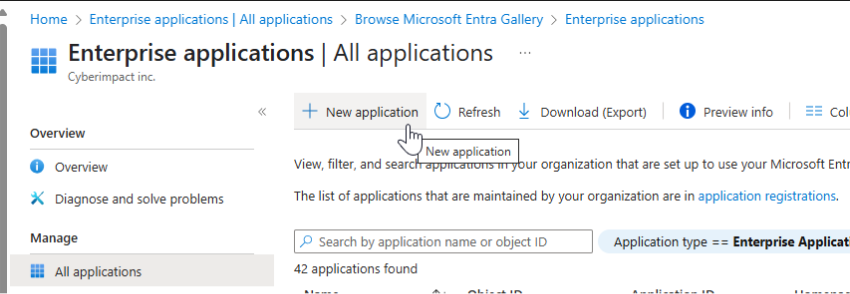
- Go to Microsoft Entra ID > Enterprise applications > New application.
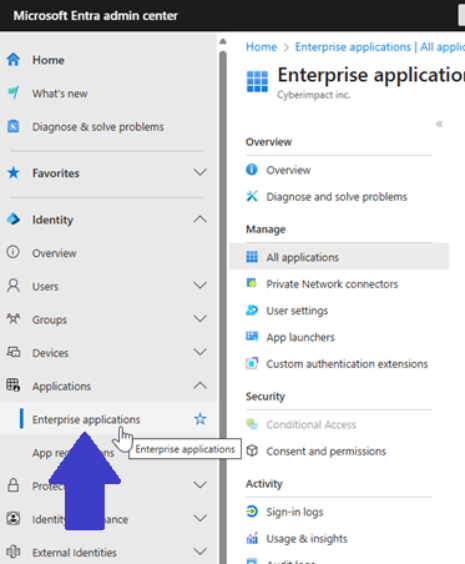
- Click Create your own application.
-
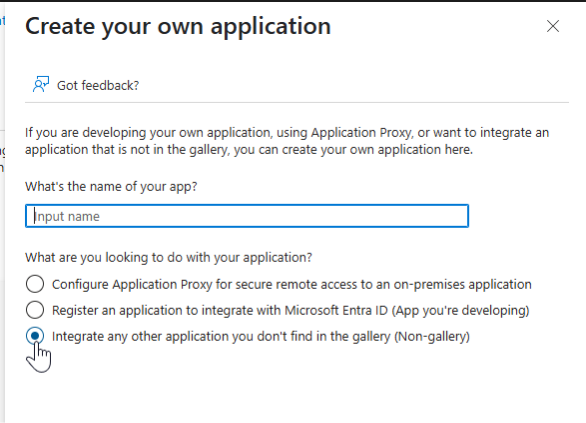
Enter a name for the application.
-
Select Integrate any other application you don’t find in the gallery (Non-gallery).
-
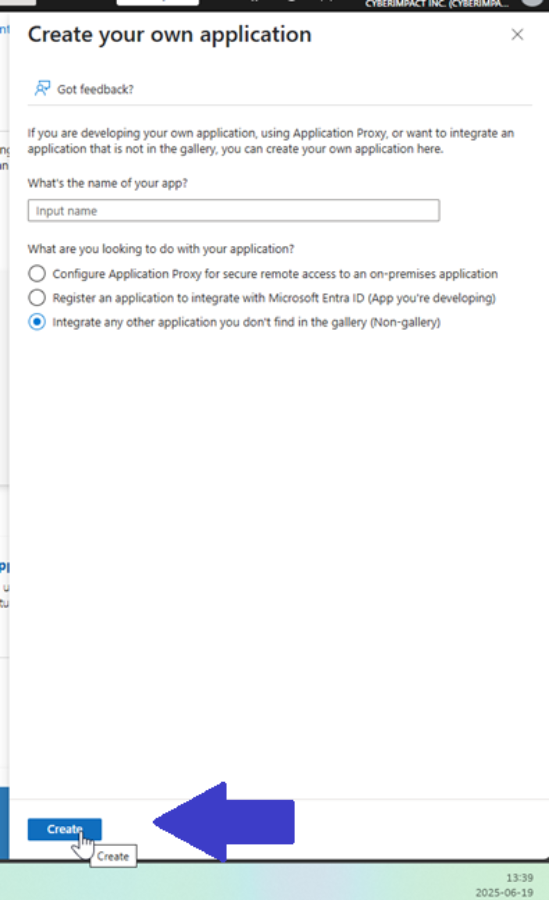
Click Create.
Configure single sign-on (SSO)
-
In the application overview, go to Single sign-on.
-
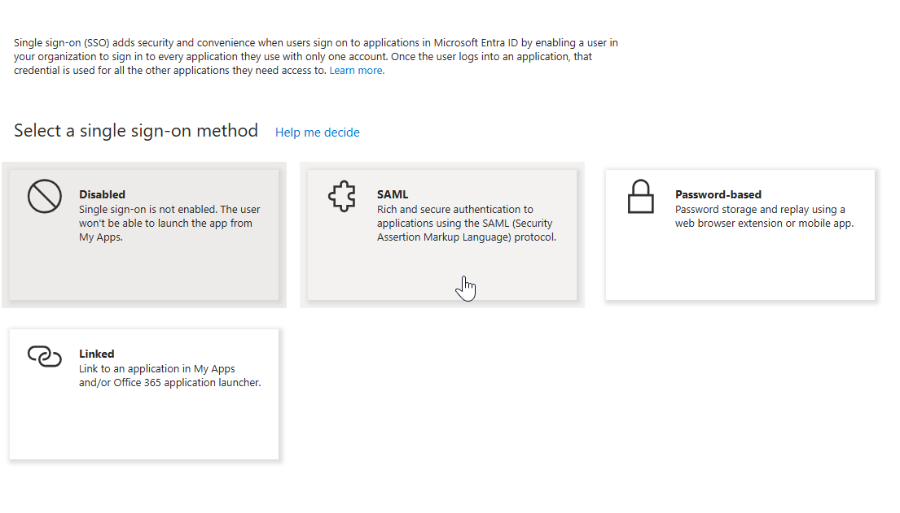
Select the SAML method.
-
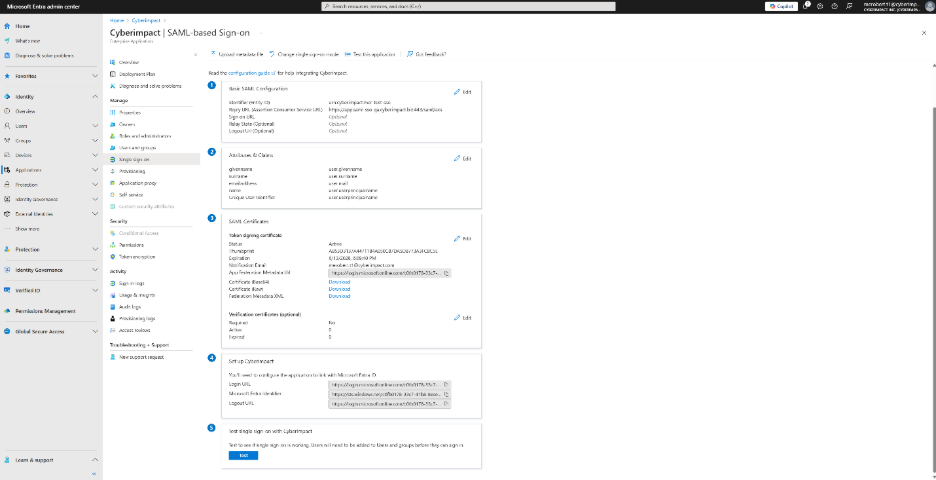
In the Basic SAML Configuration section, fill in the following fields with values provided by Cyberimpact:
- Identifier (Entity ID)
- Reply URL (Assertion Consumer Service URL
- You may leave the Index field empty.
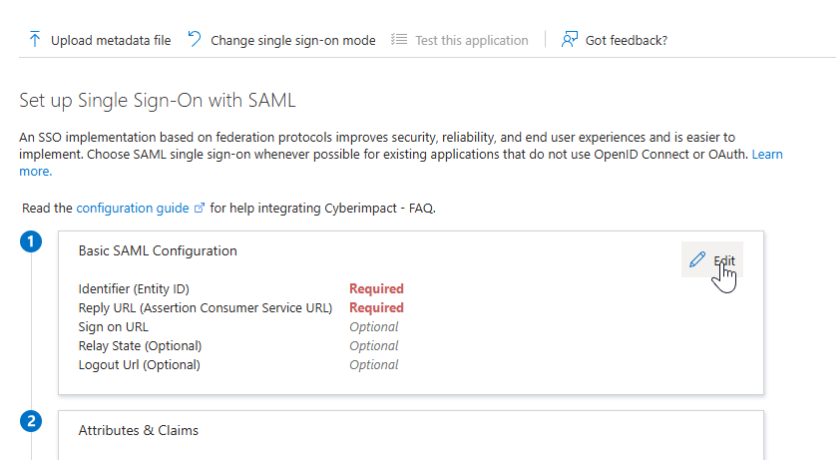
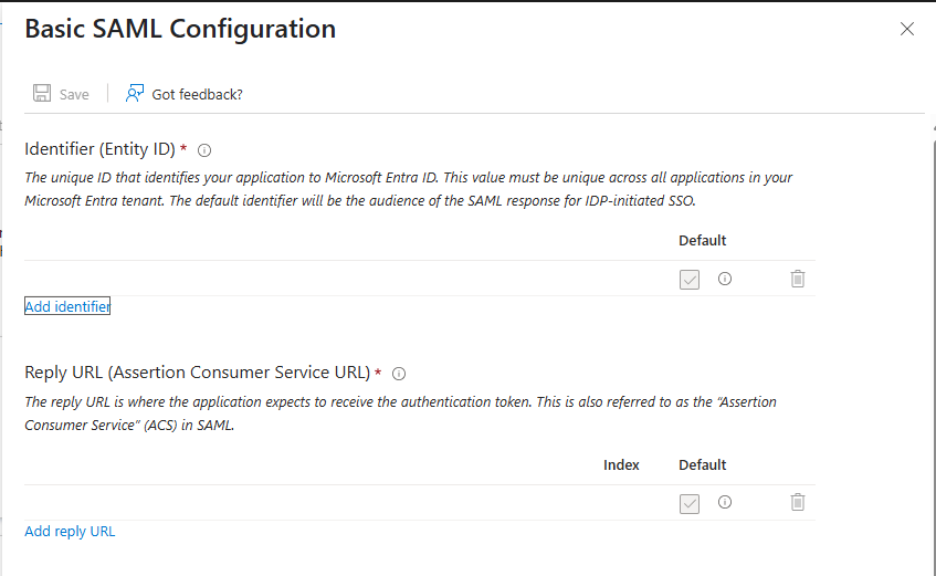
- You may leave the Index field empty.
- Click Save.
Configure attributes (Claims)
By default, Microsoft Entra ID sends attributes like user.userprincipalname. You’ll need to modify these so that Cyberimpact can match the user correctly.
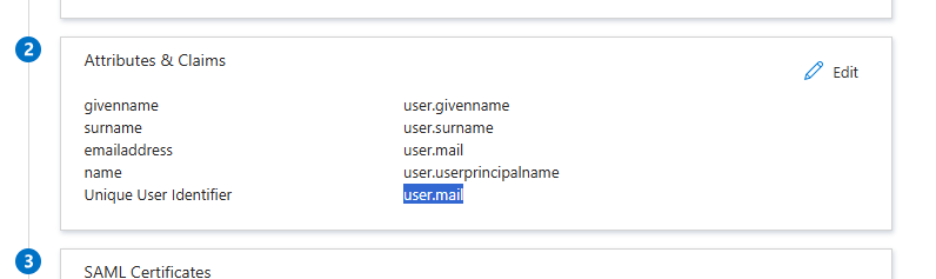
- In the application, go to Attributes & Claims.
- Click Edit.
- Set the Unique User Identifier (Name ID) to user.mail.
Send SAML metadata to Cyberimpact
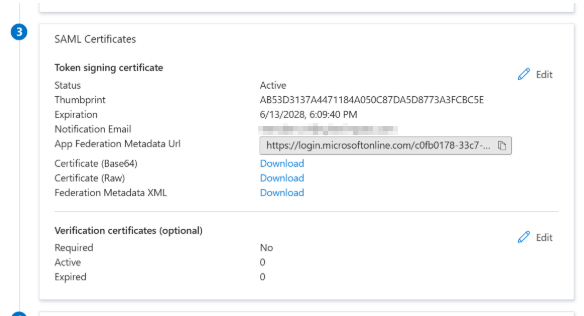
- Download the X.509 certificate (Base64 format).
- Open it in a text editor (e.g., Notepad).
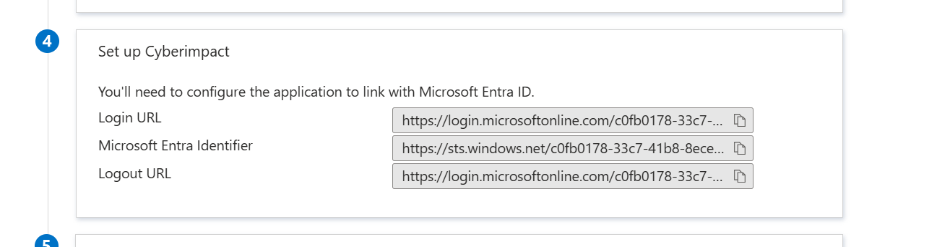
- In Microsoft Entra ID, copy the following information:
a) Microsoft Entra Identifier
b) Login URL
c) Logout URL - Upload the IdP details (IdP Entity ID, Login URL, optional Logout URL) and attach the Base64-encoded IdP x509 certificate file via a secure, access-restricted link with an expiration date (e.g., OneDrive/SharePoint/Drive) and share it with us.
- Notify our team once the information has been shared.
We will activate the SSO connection and confirm by email once setup is complete.
Assign users or groups
-
In the application, go to Users and groups.
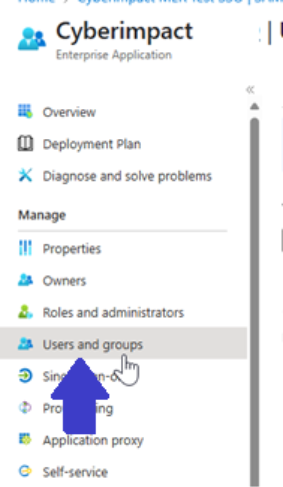
-
Click Add user/group.
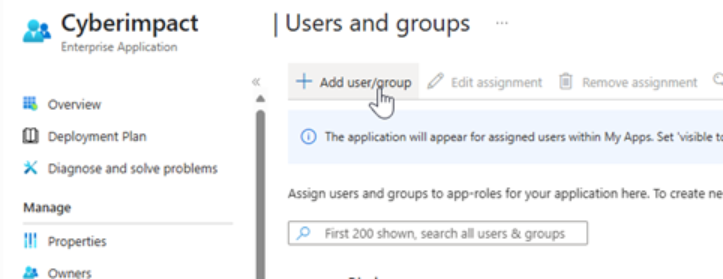
-
Under the Users section, click None selected.
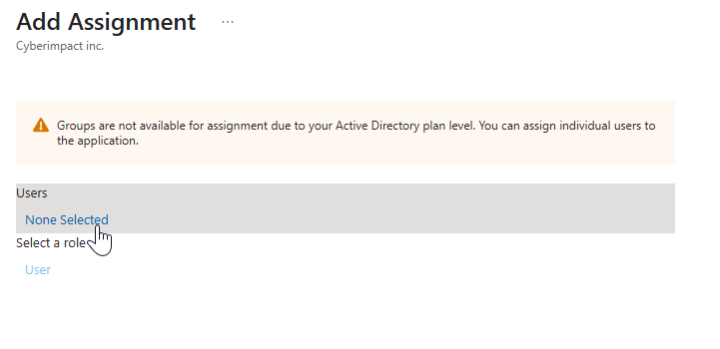
-
Search for and select the users or groups to grant access via SSO.
-
Click Select, then Assign.
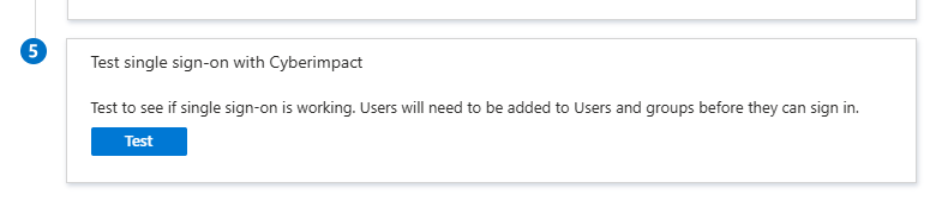
Test the connection
You can test the connection via:
- The Microsoft Entra portal
- The direct login URL
- Or the Test single sign-on section in the application configuration (in Microsoft Entra ID)
Need help?
Our support team can assist with configuration (SAML in Entra ID, attribute mapping, metadata sharing) and testing.
Contact our team
Sign in with SSO
Once your SSO setup is completed and tested, you can switch users to this access method for everyday use. It’s expected that the Cyberimpact login page does not show an SSO button yet—access happens from your identity provider (IdP) or your intranet.
To sign in:
-
Open your organization’s portal (e.g., Microsoft Entra ID app portal, Okta, OneLogin, etc.).
-
Click the “Cyberimpact” tile or use your IdP’s SSO login address (IdP Login URL) provided by your IT team.
-
Complete authentication on the IdP side (MFA, internal policies), and you’ll be redirected to Cyberimpact.
-
Enter your Cyberimpact 2FA code (required). If you mark your device as trusted, you won’t need to re-enter the code for 30 days on that device.
Don’t see the Cyberimpact tile in your portal?
Contact your IT team to be assigned to the application.
